Disguise the information in such a way that it meaning make a unintelligible to an authorized person. So we have many way to prevent oth
::Cryptography Terminology
::Cryptography Algorithm

qAsymmetric algorithms P=D(Kd, E(Ke, P))
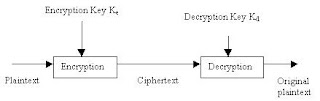
Slide 16 
Slide 17 Slide 17
* a strong encryption algorithm
* a secret key known only to sender / receiver
2) mathematically have: C = EK(P) P = DK(C)
3) assume encryption algorithm is known implies a secure channel to distribute key
Slide 19 

Symmetric Cryptography Principles

Symmetric Cryptography Requirements
q
1 ) two requirements for secure use of symmetric encryption:
* a strong encryption algorithm
* a secret key known only to sender / receiver
2) mathematically have: C = EK(P) P = DK(C)
3) assume encryption algorithm is known implies a secure channel to distribute key
Encryption using Asymmetric Cryptography

Methods use in Cryptography Algorithm
¨
Substitution
a) monoalphabetic substitution
- Formed by shifting the letters of the original alphabet
b) polyalphabetic substitution
- Extension of monoalphabetic substitution system
- Using Vigenere Tableau
Transposition
a) unkeyed transposition
- Rearrange letters by using matrix
b) keyed transposition
- Rearrange letters by using matrix where the size of matrix is determined by the length of the key used.

No comments:
Post a Comment